 IoT-driven Transformation and the Blurring Line Between the B2B and B2C Markets
IoT-driven Transformation and the Blurring Line Between the B2B and B2C Markets

IoT market is opening up new business opportunities. Enterprises should focus on whatever IoT functions they can utilize to their advantage and maximize their value, rather than on whether their organization gains from IoT adoption.
IoT is used by customers in various facets of their businesses, including data collection from remote meters, automation and control of heating equipment, car tracking and entertainment management, pet tracking, and a host of other applications. New examples emerge continuously, necessitating the help of a flexible and knowledgeable partner.
Comarch entered the IoT market at the outset, and has continued to develop its fundamental products and services to produce a complete portfolio that will enable digital service providers to establish the strongest position possible in this demanding market. What can the Comarch IoT Ecosystem help you accomplish?









"MAC Conformance Test Tool" demo for FiRa Consortium

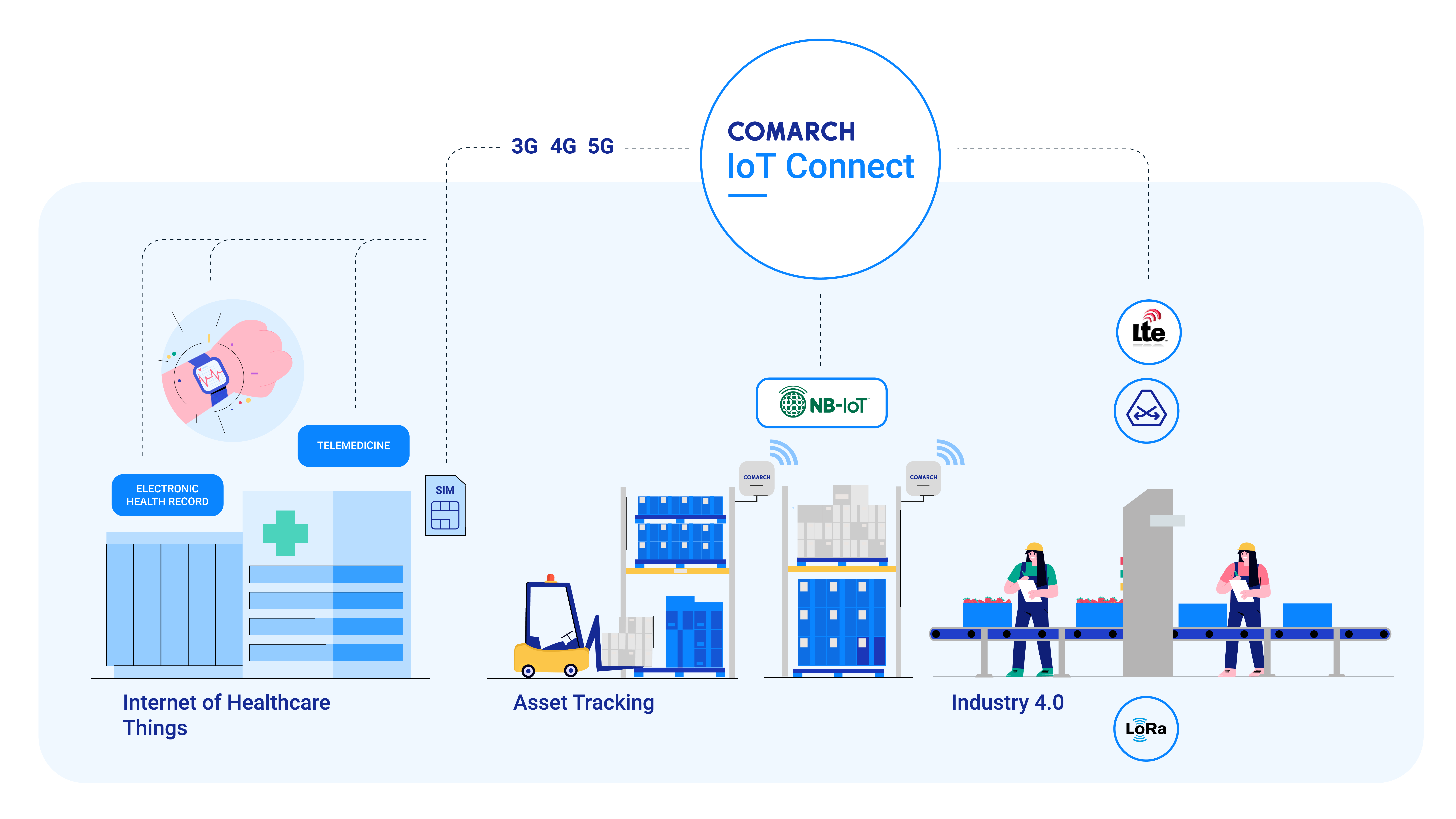
Comarch for e-Mobility

Comarch Telecare System

Comarch IoT Plant

Industry 4.0

Digitization of production

Beyond the Basics of IoT A Practical Guide to Sales Automation

Comarch IoT Plant

Internet of Production

Paving the Way for AI in IoT


















Please wait