 Comarch Identity and Access ManagementControl the access to your assets and personal data
Comarch Identity and Access ManagementControl the access to your assets and personal data
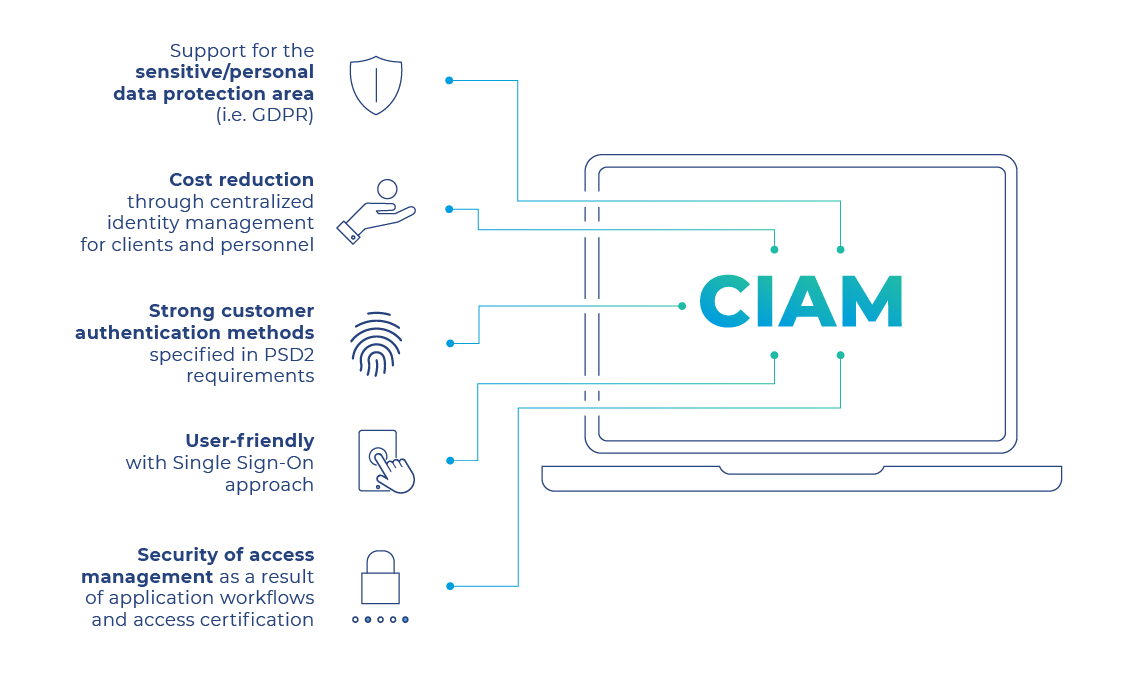
Support your GDPR compliance

Comarch Identity & Access Management (CIAM) combines the functions of Identity Management and Access Management systems. It allows for a full control over the access to company's applications, workstations and VPNs.
Comarch Identity & Access Management comes with world-class methods for authentication, authorization, identity lifecycle and accountability. Its modular architecture makes it easy to adapt to specific types of organizations across hierarchies and geographies.
The system supports organizational workflow procedures and keeps all user accounts in all applications up-to-date. On top of that, it offers a smooth integration for access management and authorization purposes.
CIAM easily integrates with multiple devices and applications for strong authentication and authorization including smart cards, cryptographic certificates or hardware and software tokens. This fact significantly extends its use case scenarios.
Comarch Identity & Access Management may be used for adjusting role and access permissions, granting remote access to company’s IT resources or delegating privileges. It also provides vital assistance in meeting the GDPR and PSD2 requirements.
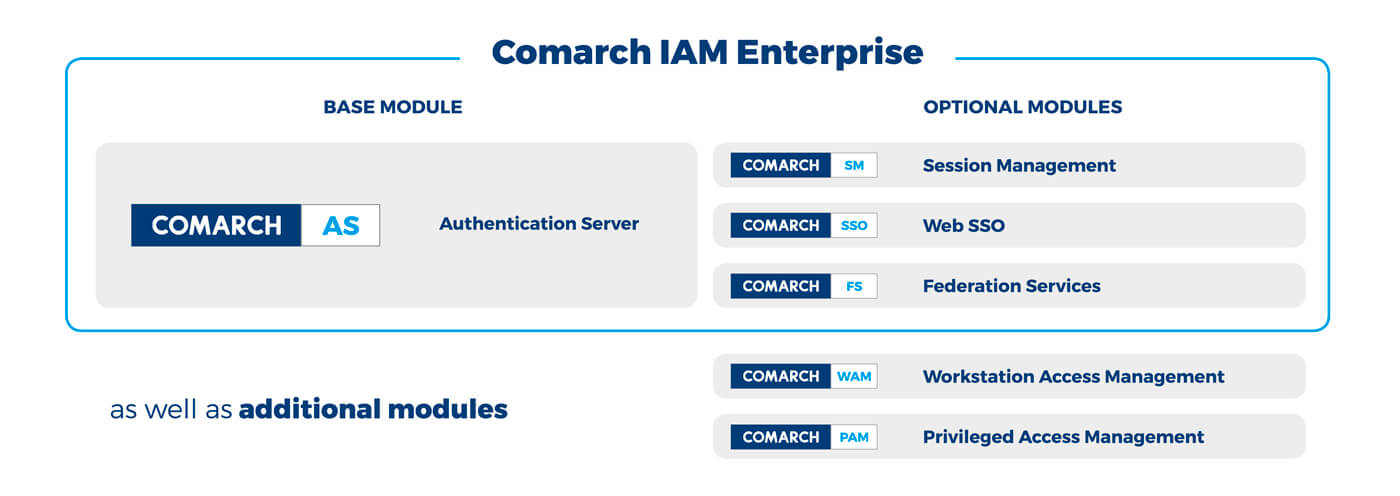
Comarch IAM comes with core and complementary modules that allow a customer to manage user identity and access in both small companies and large corporate enterprises.
Different modules provide customers with comprehensive services integrated under one seamless platform. There are 3 groups of modules: base, optional and additional. All of them compose the Comarch IAM Enterprise solution.
Provides support for data portability, right to be forgotten, anonymization, pseudonymization, and more
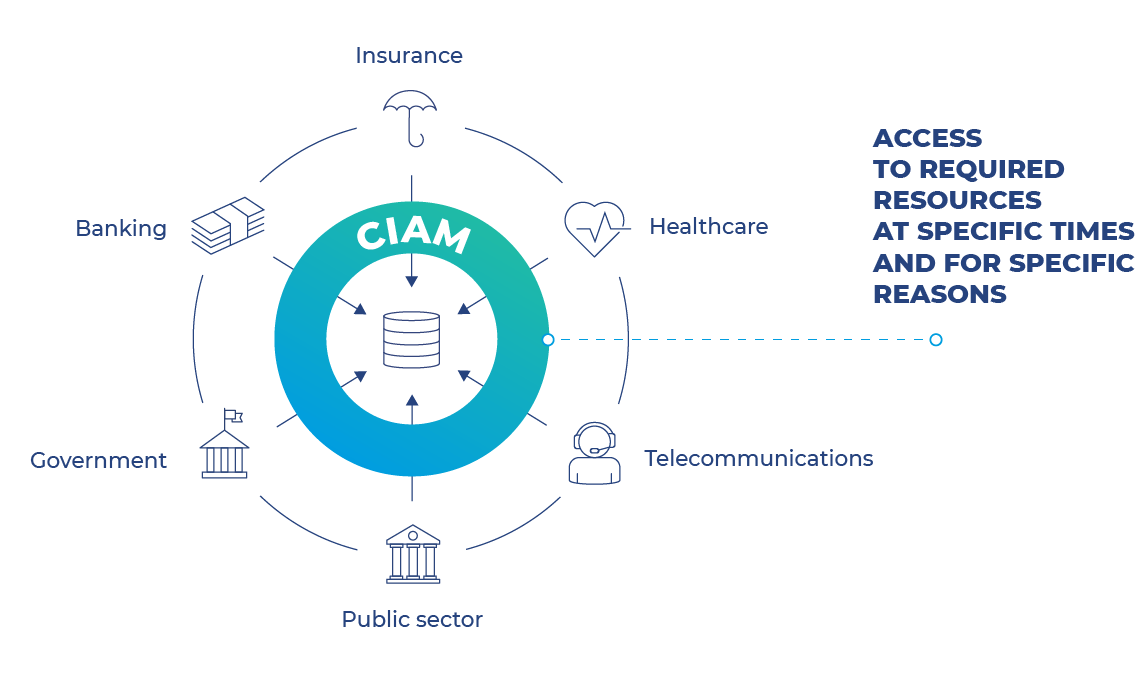
Enables appropriate persons to access the required resources at specific times and for specific reasons
Allows to manage access to systems and recourses across the entire enterprise and performs full accounting
Allow to use the four-eye principle every time a user or their supervisor requests a new permission - without using external mechanisms and eliminating paperwork
Simplifies user management and ensures high flexibility
Makes it possible to render centralized user authentication services
Allows the use of cryptographic certificates as an authentication method
Enables permission delegation to another user under constrained time horizons
Enables aggregation of all services related to user authentication and authorization data validation.
Simplifies user management and ensures high flexibility by aggregating permissions from different applications.
Allows for the management of all user identities and ensures appropriate persons have access to the required resources at specific times and for specific reasons.
Enables access to systems and resources across the entire enterprise based on the appropriate level of user permissions.
Integrates with Active Directory, LDAP and Kerberos protocols and Radius service.
Allows the use of cryptographic certificates as an authentication method.
Supports industry standards, such as SAML and OpenID Connect.
Helps reflect the organizational structure and allows for using the four-eye principle every time a user or their supervisor requests a new permission









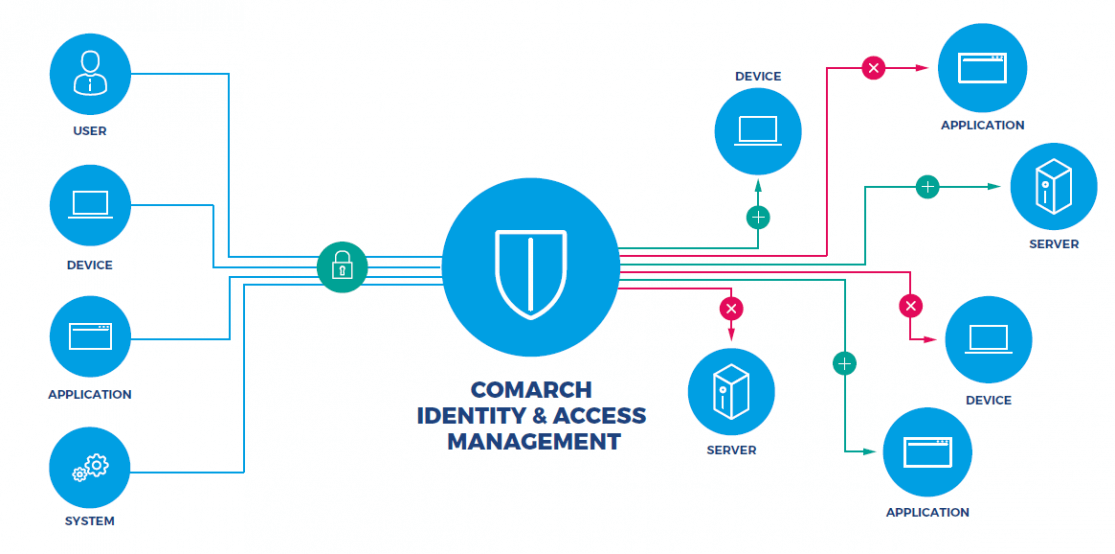
The following diagram illustrates the position of the CIAM platform in the enterprise infrastructure and the importance of identity management software and access management software for protected data access.

Integrated applications no longer need to perform user authentication: instead, the Comarch IAM Authentication Server is used for verifying the credentials. Authentication methods, required by each application, can be adjusted on the fly.
Below you can find the list of authentication methods available out of the box. Thanks to open architecture, it is possible to easily integrate additional methods (e.g. used by tokens of other vendors such as Vasco/OneSpan or Gemalto).
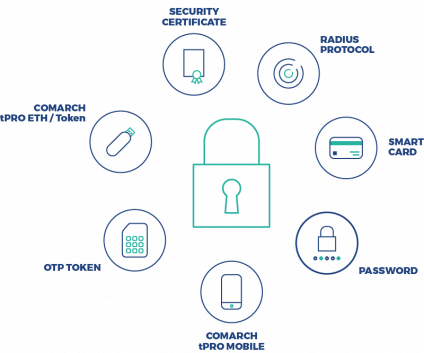
Integrated applications no longer need to perform user authentication: instead, the Comarch IAM Authentication Server is used for verifying the credentials. Authentication methods, required by each application, can be adjusted on the fly.
Below you can find the list of authentication methods available out of the box. Thanks to open architecture, it is possible to easily integrate additional methods (e.g. used by tokens of other vendors such as Vasco/OneSpan or Gemalto).

Allows user to access multiple web applications with one set of login credentials.
Provides support for data portability, right to be forgotten, anonymization, pseudonymization as well as PSD2 requirements
Allows users to complete some administrative tasks by themselves, such as changing the password, or assigning a new token or mobile phone.
Enables permission delegation to another user under constrained time horizons.
• Centralized and efficient access control policy
• Reflection of company’s organizational structure
• Delegation of authority (user permissions may be passed on to another user in a time-constraint manner)
• Management of user and device identities in a large number of IT systems integrated with various applications and operating systems
• Support for third-party and Comarch own authentication devices

The growing complexity of organizational structures and the increasing number of applications used at companies make user management a time-consuming and complicated task. An enterprise can solve this problem by applying a centralized identity and access management solution, minimizing both human effort and error.
Comarch IAM may be used for adjusting role and access permissions, granting remote access to company’s IT resources or delegating privileges.
The crucial beneficiaries of this solution are EU-based companies processing sensitive and transaction data in accordance with GDPR or PSD2 requirements.
The other significant capabilities of the CIAM solution are:
Tell us about your business needs. We will find the perfect solution.
The growing complexity of company structures and the increasing number of applications used at companies make user management a time-consuming and complicated task. A company can solve this problem by applying a centralized identity and access management solution, minimizing both human effort and errors.
The main beneficiaries of this solution are EU-based companies processing personal and sensitive data. Comarch IAM may be used for adjusting role and access permissions, granting remote access to company’s IT resources or delegating privileges. It also provides vital assistance in meeting the GDPR requirements.
Tools and features designed for efficient customer acquisition, policy offering and sales
Mechanisms focused on the ongoing policy portfolio review, maintenance and support
Prospect and customer book with quick data access for efficient service and communication
Key claim functionality for servicing agents and customers requesting agent’s claim assistance
Tools for work self-planning, reminder management and task handling
Predefined reports on various aspects of user performance for self-monitoring and analysis
Knowledge base for editor management to share corporate information and documents
Access for business administrators to manage the application

Download Identity & Access Management leaflet
Find out how to fully control the access to company data & infrastructure.
Tell us about your business needs. We will find the perfect solution.