 Comarch Transaction Protection - tPro MobileSmart token application for mobile banking security
Comarch Transaction Protection - tPro MobileSmart token application for mobile banking security

tPro Mobile is a mobile platform supporting strong user authentication and transaction authorization in accordance with the PSD2 directive. It consists of an external application and development libraries to be integrated with the existing products.
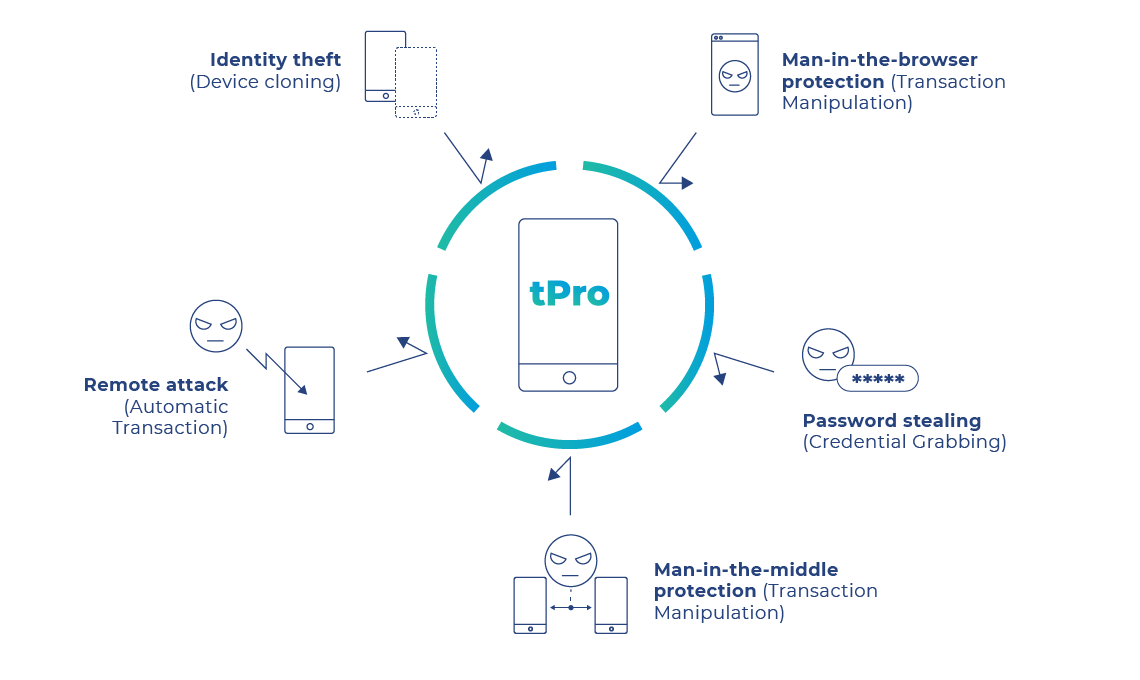
Its security mechanisms, based on strong cryptography, along with internal mechanisms analyzing the platform’s behavior ensure a high level of both security and convenience. tPro Mobile comes with a number of tools that make it difficult for third parties to launch an attack and intercept relevant data. Full OATH compatibility allows the application to be used as a second vector of authentication for services such as email and social networks.

The platform provides a wide range of authentication mechanisms, from traditional PIN codes up to fingerprint and face recognition authentication. With full OATH compatibility, tPro Mobile can be used as an additional component of 2FA authentication for critical resources such as email, administration panels, and social media. Using programming libraries that come with the platform, it is also possible to integrate tPro Mobile with the existing products quickly.
What you see is what you sign – this, in short, is the principle the tPro Mobile platform builds upon. Its real-time threat detection mechanisms allow you to easily spot potentially dangerous factors such as configuration gaps and suspicious activities in the platform itself. Interactive data entry protects you against switching key transaction data, e.g. such as IBAN or transfer amount. The information on activities within the protected resources is delivered to you by means of a PUSH notification (instead of text message). The solution architecture along with the pairing procedure protect you from the platform being cloned and accessed by unauthorized third parties. The offline mode lets you generate the authorization code for transactions even if your device is out of range. Additionally, the tPro Mobile solution implements a number of mechanisms that hide information about the results of security-sensitive operations (such as entering a PIN code).
In order to minimize the fraud risk, tPro Mobile comes with various transaction authorization variants. From a standard variant – which takes pressing a button – up to an interactive one where the user is asked to re-enter portions of critical data before confirming a transaction. Such a scenario allows the user to be involved in the process of transfer authorization so that potential anomalies can be detected before the actual money is sent. tPro Mobile can also store transactions offline by means of dynamically generated authorization code. Apart from strong cryptography, the user security is also ensured by a number of monitoring mechanisms detecting threats in real time.


tPro Mobile offers strong customer authentication and transaction authorization using the HOTP, TOTP and OCRA algorithms adopted by the Initiative for Open Authentication (OATH).
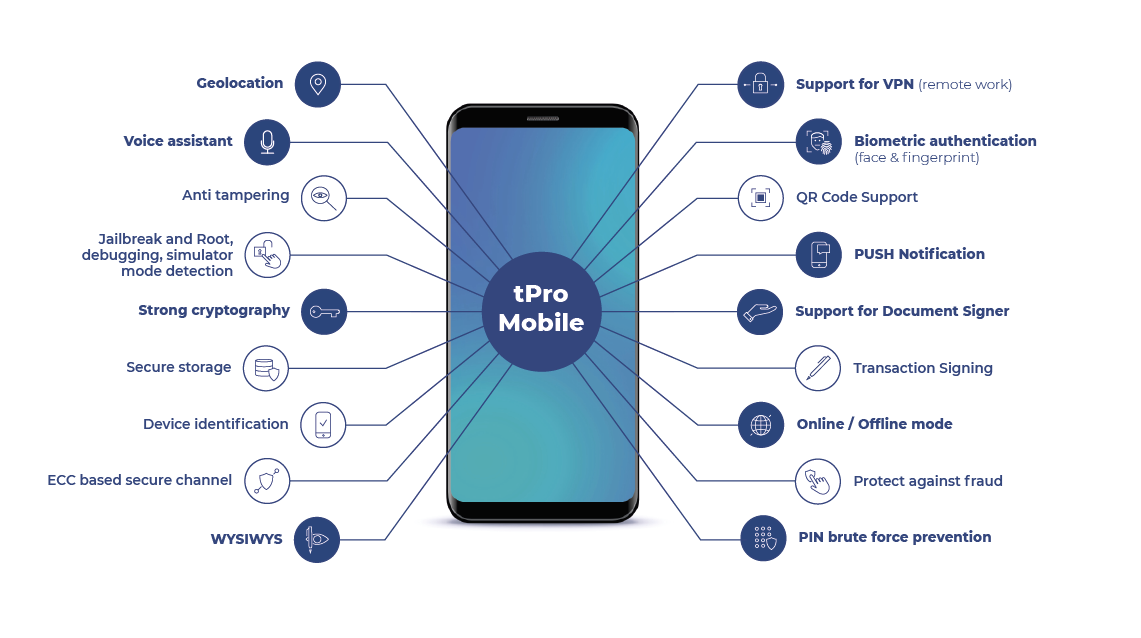
L.p. | Feature name | Feature description | SDK | Application |
1. | Voice assistant | Leads you through the application using voice instructions | X | V |
2. | Anti tampering | Detects suspicious activity in real time | V | V |
3. | Strong cryptography | Protects user keys with strong cryptography algorithms when TPM is unavailable | V | V |
4. | Secure storage | Uses dedicated hardware storage for critical data | V | V |
5. | Device identification | Prevents spoofing with persistent identification | V | V |
6. | Device binding | Links users to authorized devices | V | V |
7. | ECC based secure channel | Encrypts communication to the end server by ECC cryptography | V | V |
8. | WYSIWYS | What you see is what you sign | X | V |
9. | Face authentication | Authenticates with facial recognition | V | V |
10. | Fingerprint authentication | Authorizations with fingerprint | V | V |
11. | QR Code Support | Supports secure pairing via QR codes | V | V |
12. | PUSH Notification | Uses push notifications instead of legacy technologies like text messages | X | V |
13. | Transaction signing | Protects transaction data using strong cryptography | V | V |
14. | Online/Offline mode | Allows user authentication and transactions authorization when mobile phone is offline | V | V |
15. | Interactive mode | Requires retype part of IBAN and amount to protect against fraud | V | V |
16. | PIN hint | Informs user in a secure way about potential mistake during PIN code type | X | V |
17. | PIN brute force prevention | Attacker cannot distinguish if entered PIN is correct or wrong | X | V |

Download tPro Solutions leaflet
Read more about how to protect your customers from internet frauds









Tell us about your business needs. We will find the perfect solution.