
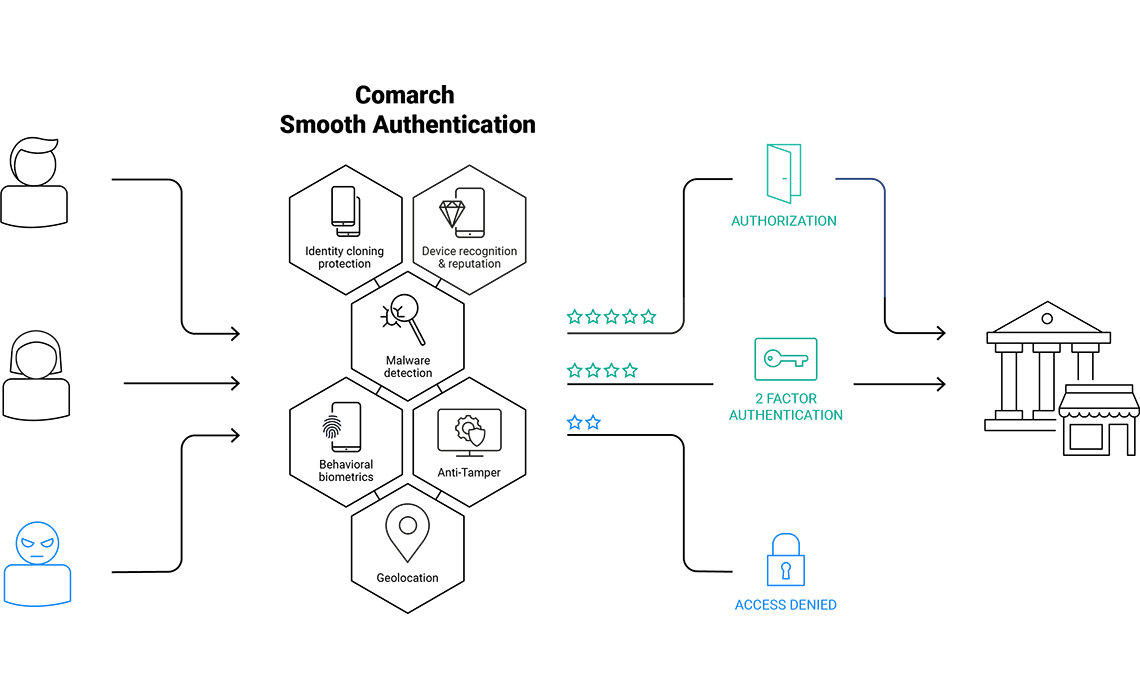
Comarch Smooth Authentication is a risk-based authentication software that combines device recognition, malware detection, and behavioral biometrics capabilities in order to detect frauds in real time. Risk-based authentication allows you to grant your customers with secure and truly frictionless customer journey. It provides exceptional protection from online frauds while building your position as a trustworthy partner.

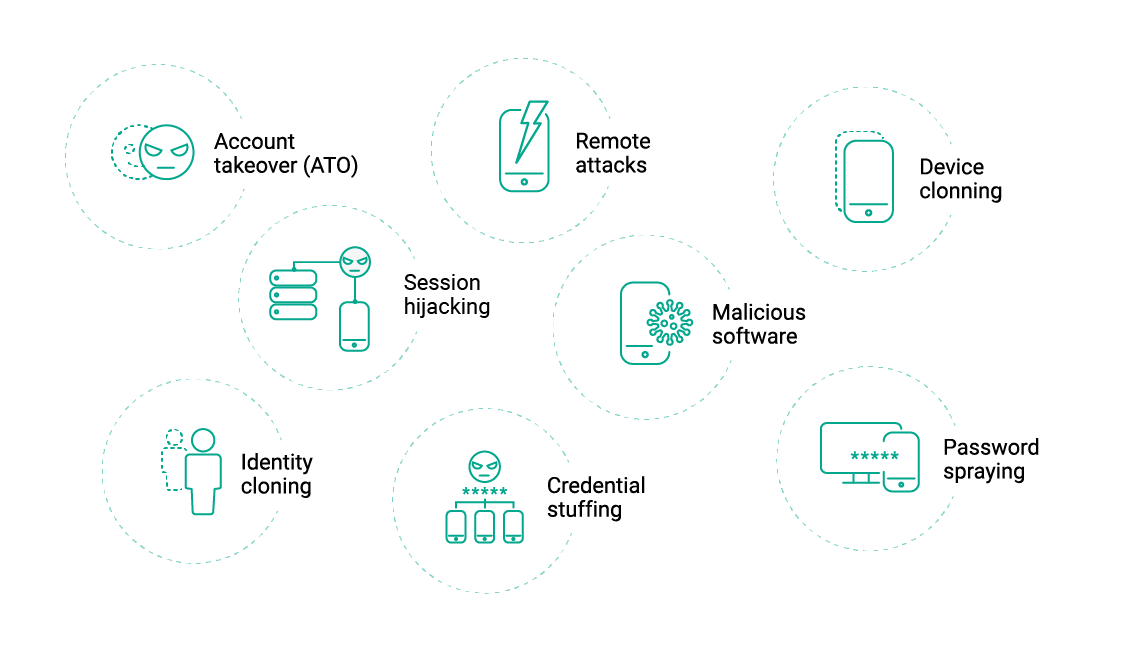
Detect Account Take Over (ATO) attempts in real time
Distinguish cyber criminals from legitimate users

Provide secure application environment to your customers and keep top-level usability
Customers expect secure operations with your application. But forcing them to constantly verify their actions with PIN codes, one-time passwords, tokens, etc., impacts their experience and causes a significant decrease in conversion rate. Why not make the authentication and authorization process smooth with a risk-based authentication software, operating constantly in the background without involving the end user?
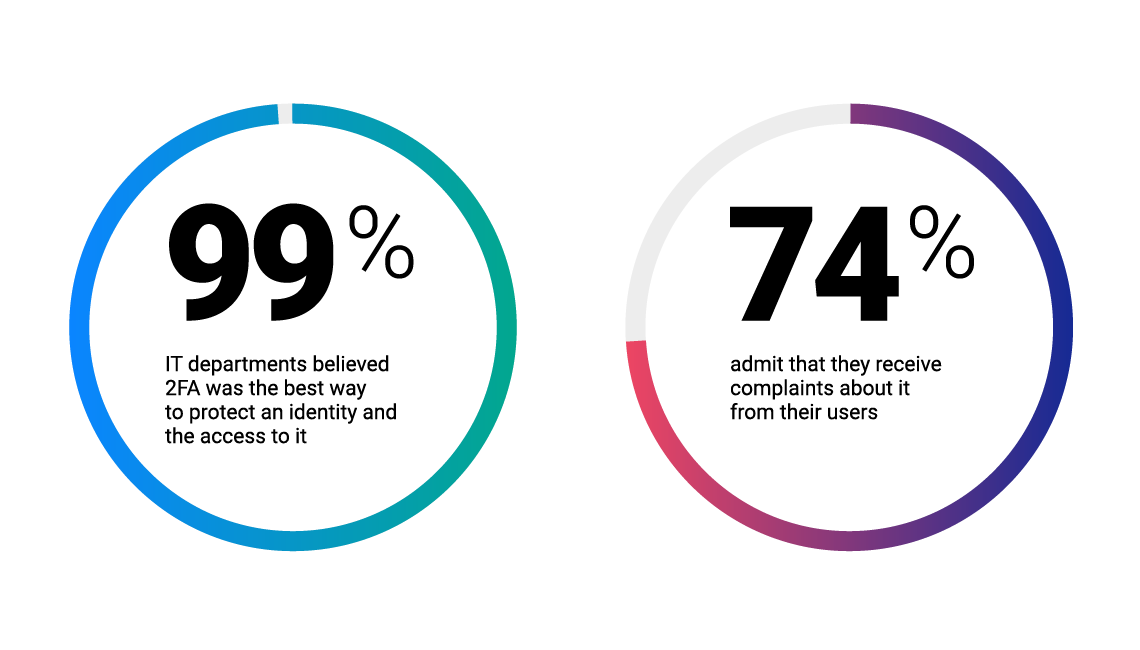
source: Betanews
Comarch Smooth Authentication software analyzes multiple artifacts coming from end user devices, behavior, and software installed on user devices, in order to calculate risk rating for each transaction. This concept of adaptive, risk-based authentication allows to strike balance between security and usability – the second factor is used only when explicitly needed and end customers can enjoy frictionless experiences.

Comarch Smooth Authentication software is made for every company that provides their customers or employees with mobile or web access to their services. The risk-based authentication approach lifts fraud protection to the next level in:

We won’t leave you alone with your questions. By implementing our effective Smooth Authentication software, we will also provide you with knowledge and experience in cyber security. Our enthusiastic cyber security team constantly monitors the latest fraud scenarios, and our team of ethical hackers tirelessly works on detecting and fighting up-to-date threats in our dedicated Malware LAB. All that so you can benefit from the risk-based authentication software that responds to the newest cyber security challenges.

Our product R&D team consists of developers experienced in cyber security, dev-ops and penetration testers. These teams challenge each other in agile sprints, to develop the most advanced fraud detection techniques. Thanks to this approach, our risk-based authentication solution is well-tested against the ingenuity of fraudsters and hackers – in a similar fashion to Red Team / Blue Team-simulated cyberattacks.
Download the Comarch Smooth Authentication leaflet

Download Comarch Smooth Authentication leaflet
Read more about how drive your security by risk-based authentication









Tell us about your business needs. We will find the perfect solution.